With Ocelot, removing blind spots in your infrastructure management and detecting vulnerabilities in advance is easy
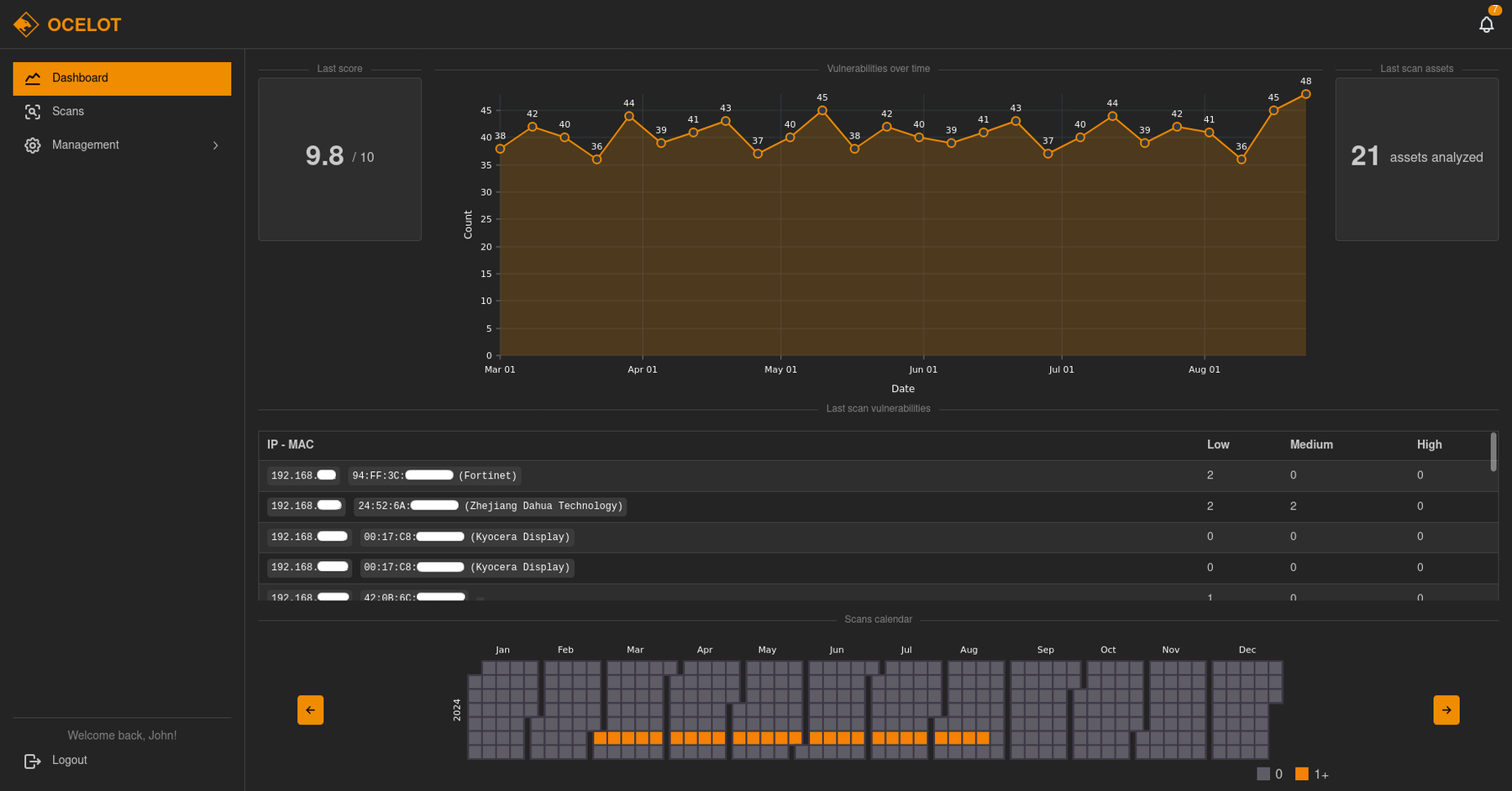
Know your security posture
Because prevention is the best defense
Knowing your network is the first step towards optimizing it. Detect undocumented devices or wrong network configurations in a few clicks!
Remove risks by immediately knowing when obsolete or insecure devices are present in your network.
Asset inventories and detailed vulnerability reports simplify auditing processes in your company.
Flexible and Powerful
Let Ocelot do the heavy lifting for you
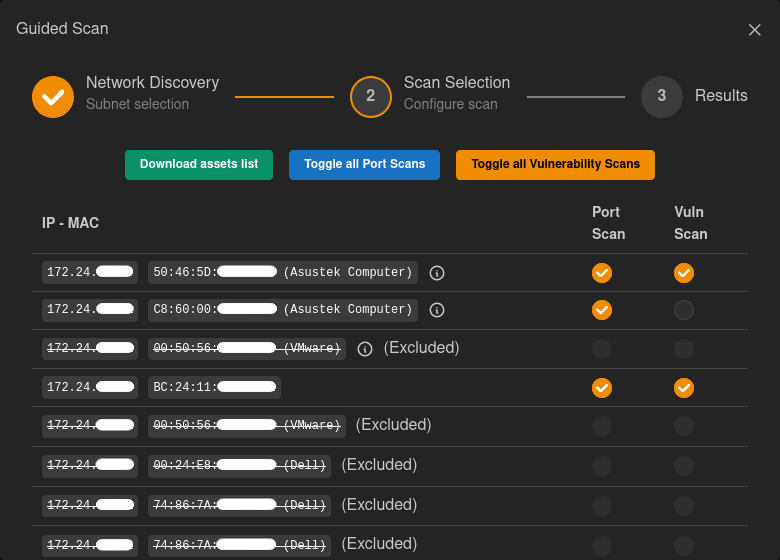
Configure exactly what needs to be scanned and when. A lightweight port scan allows you to see what's on your network, while a full vulnerability scan detects potential risks in your network. With the ability to plan multiple recurring scans, it is possible to analyze productivity-critical devices outside business hours, for extra peace of mind.
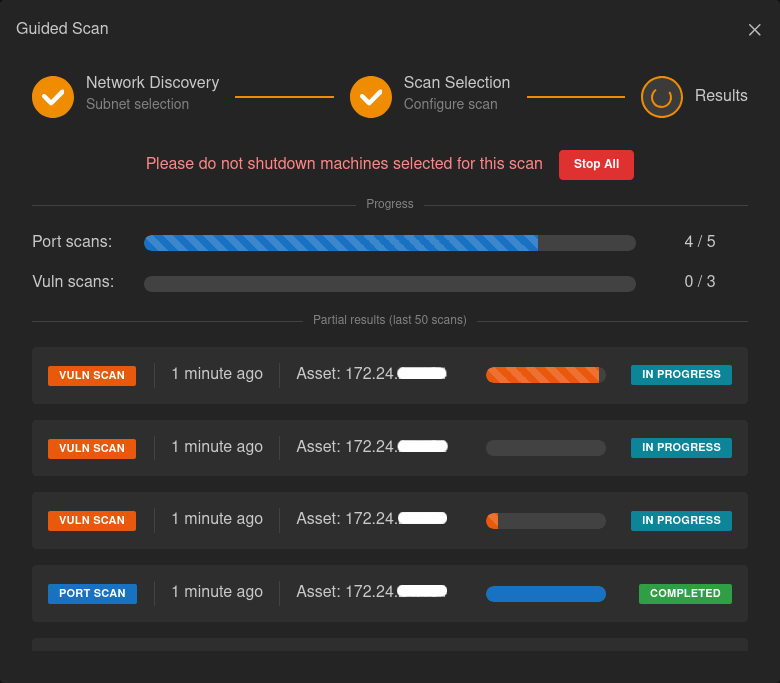
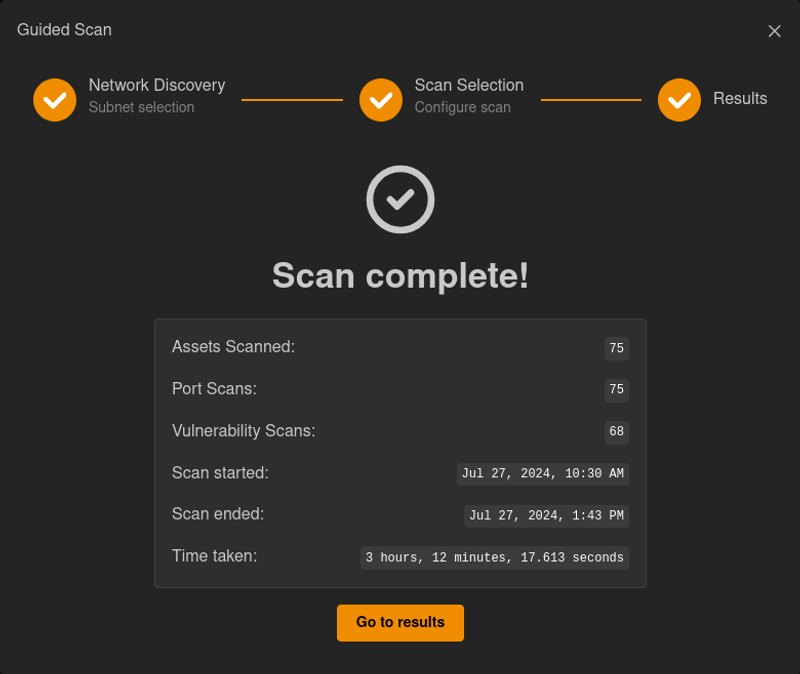
Once configured, Ocelot works autonomously and makes full use of hyper threading to perform parallel scans as fast as possible. Once a scan completes, a quick overview is immediately presented, while a customized report will be emailed to you after a few days.
Contact us to book a demo or ask further questions. You can also find more information by downloading our free product flyer.